See the Platform
Real dashboards from the Optimal Platform showing Launch Pad, Vulnerability Management, STIG Library, and Container SBOM tracking.
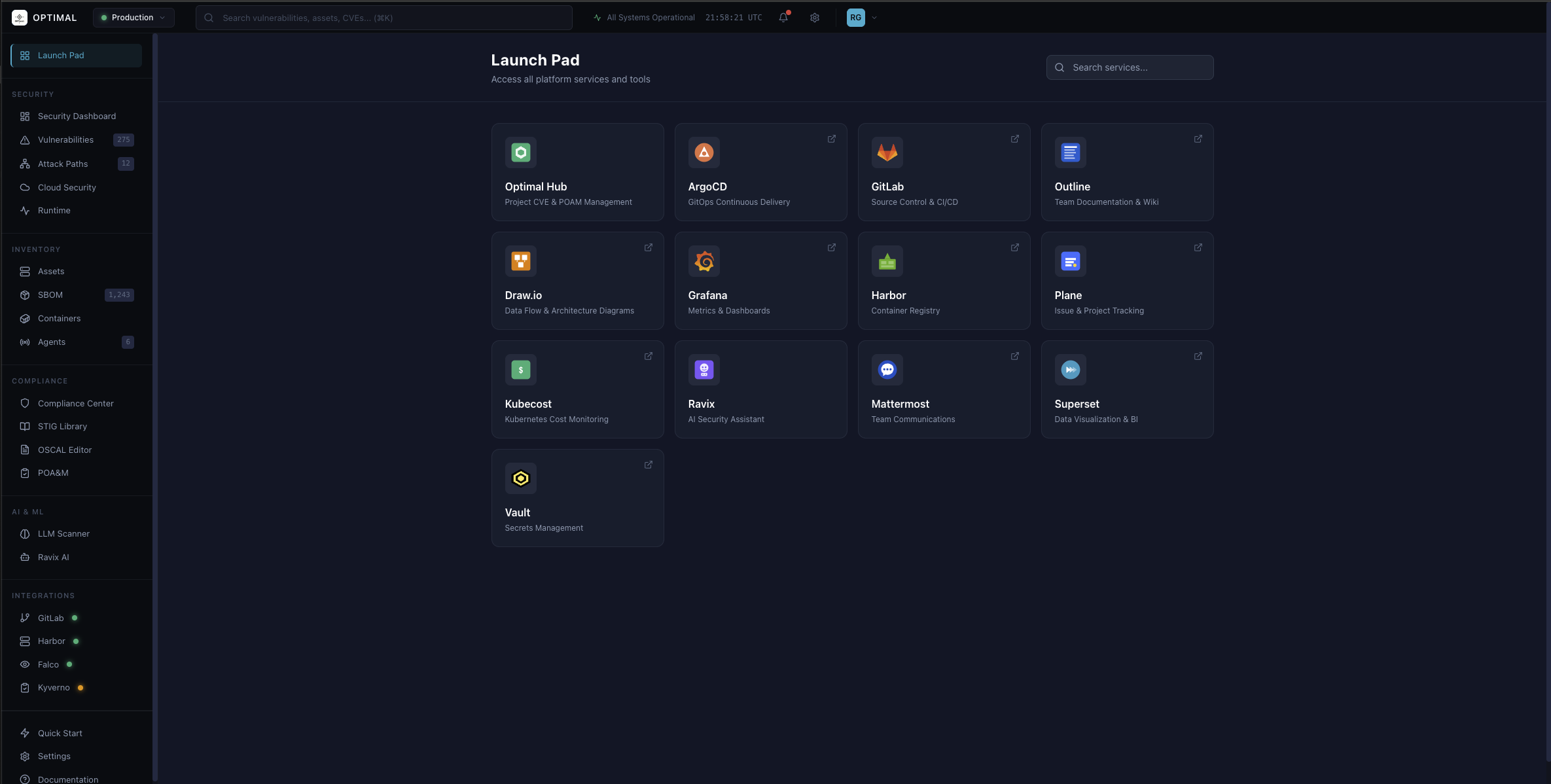
Launch Pad
Access all platform services and tools from a single unified interface. Integrated security dashboard, compliance center, and DevSecOps toolchain.
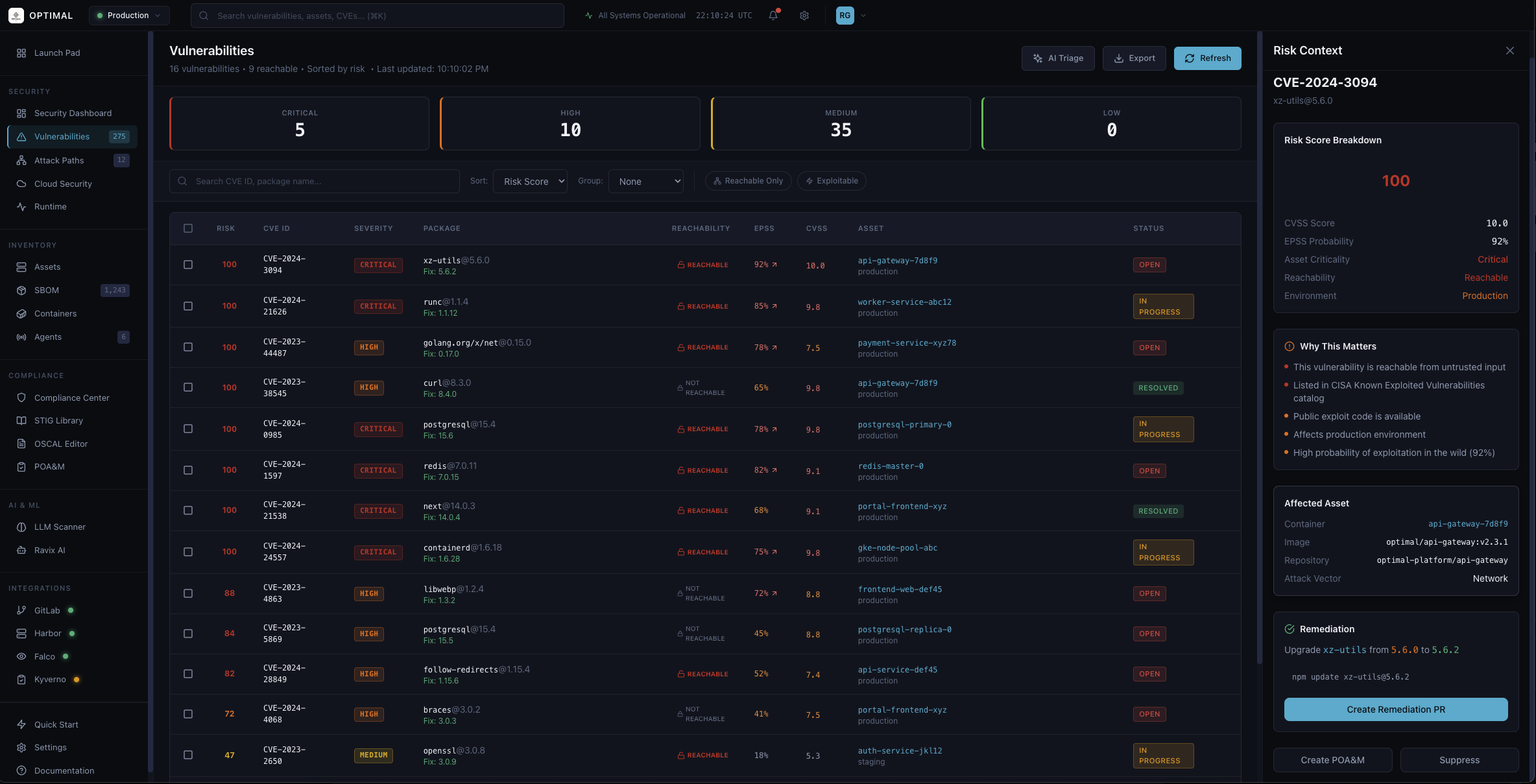
Vulnerability Management
AI-powered risk scoring with reachability analysis, EPSS probability, and CISA KEV integration. Know which vulnerabilities actually matter to your production environment.
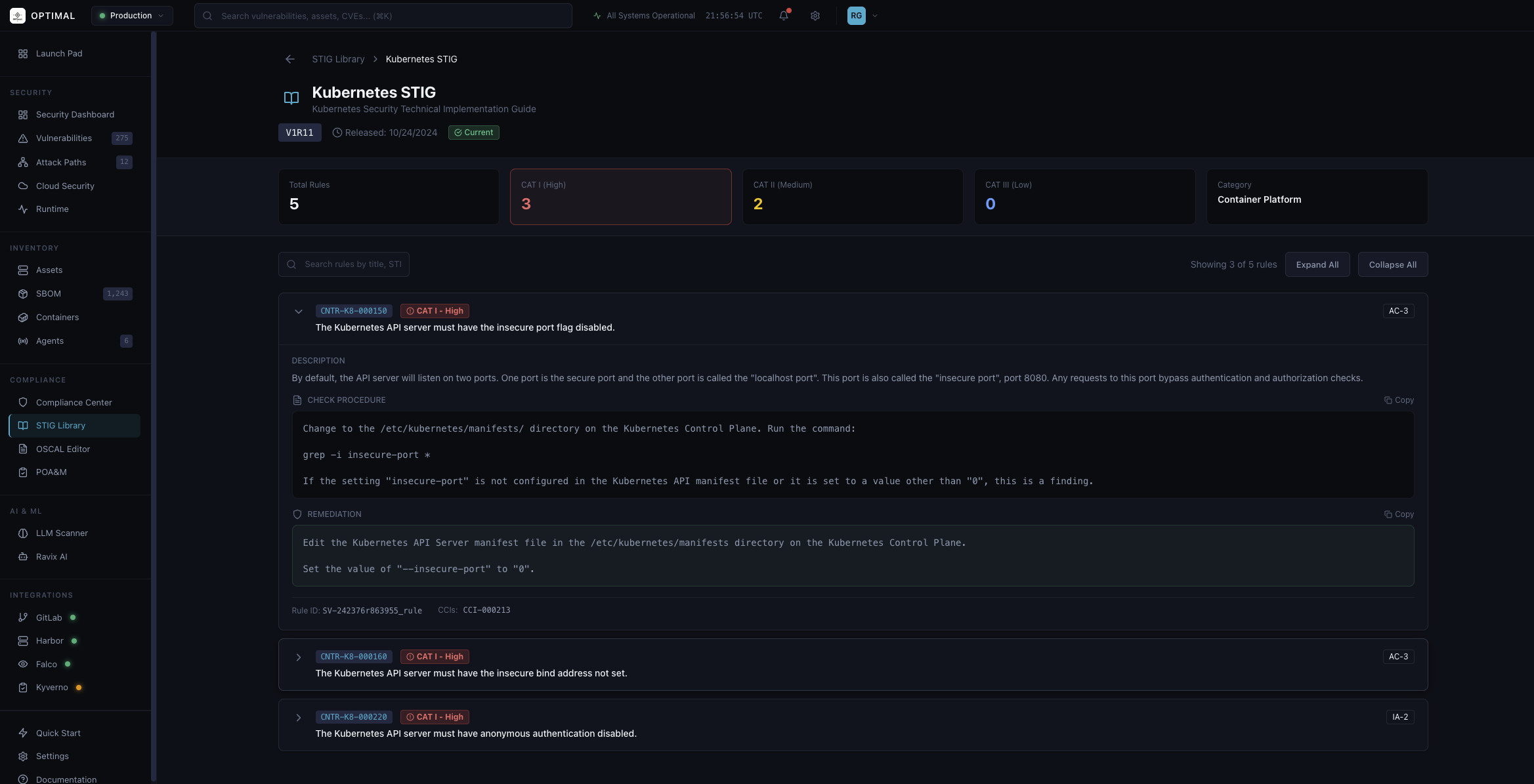
Kubernetes STIG
Container platform security compliance with DISA Kubernetes STIG checks, CAT severity mapping, and automated remediation guidance.
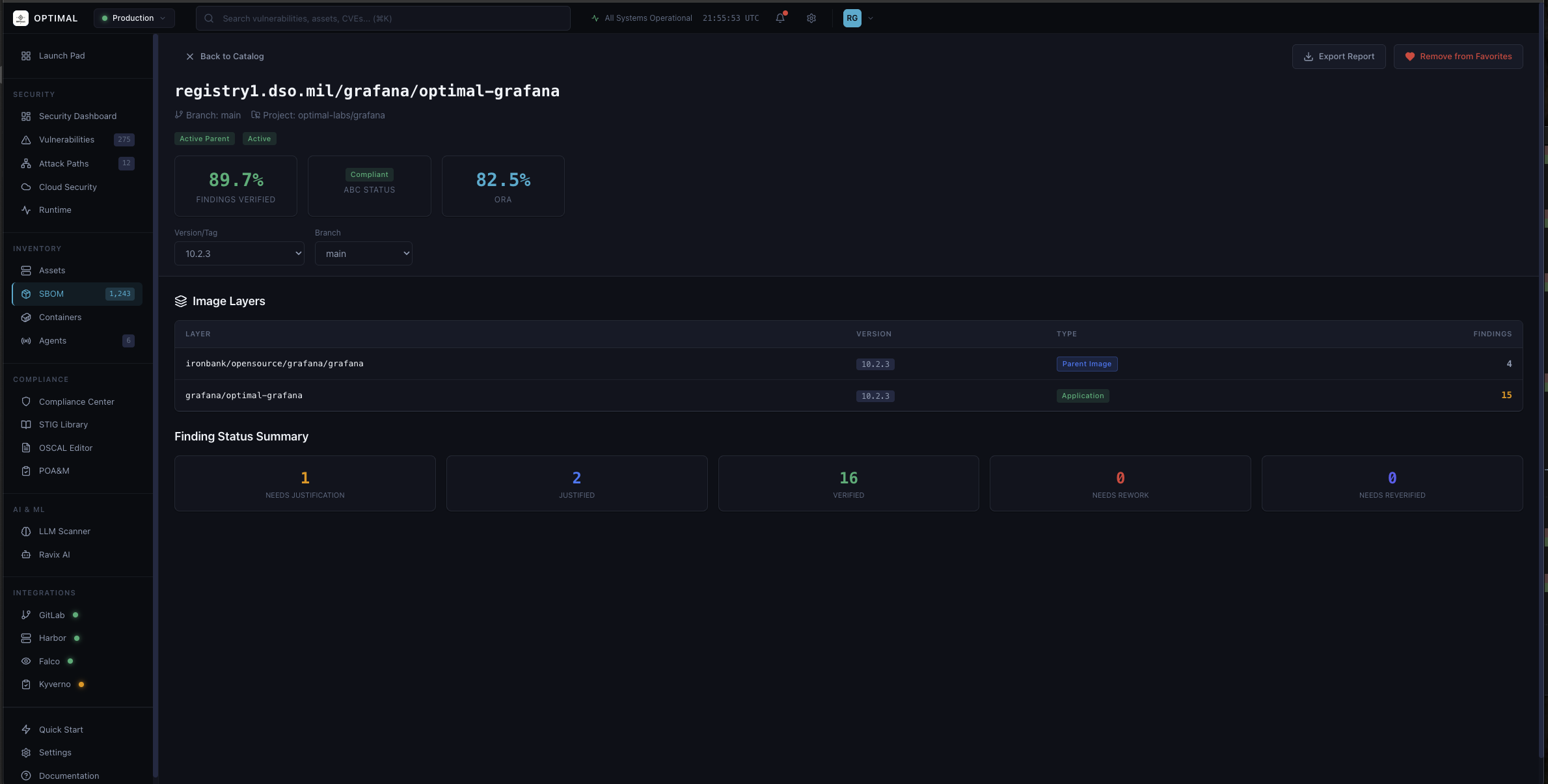
Container Image Catalog
Complete container registry visibility with image layer analysis, ABC compliance status, and ORA scoring. Track findings from Iron Bank parent images through your application layers.
